I have a nodejs app running on AWS deployed using AWS Opsworks. The app relies on an AWS IoT certificate and AWS IoT private key being present and I don’t want to add the key and certificate to my git repo.
The solution I ended with was to use the AWS Opsworks App environment variables to pass in the certificate and key as environment variables and read these from the nodejs app.
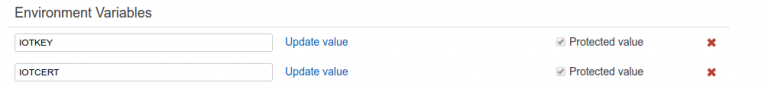
Opsworks replaces all new line characters with spaces so in our app we have to reverse this:
var iotcert = process.env.IOTCERT;
var iotkey = process.env.IOTKEY;
iotcert = iotcert.split(" ").join("\n").replace("BEGIN\nCERTIFICATE", "BEGIN CERTIFICATE").replace("END\nCERTIFICATE", "END CERTIFICATE");
iotkey = iotkey.split(" ").join("\n").replace("BEGIN\nRSA\nPRIVATE\nKEY", "BEGIN RSA PRIVATE KEY").replace("END\nRSA\nPRIVATE\nKEY", "END RSA PRIVATE KEY");
…. Problem solved 🙂
I suppose it is a little less secure than the certificate and key being on the file system and with read only access to the nodejs process but it’s a lot more secure than the certificate and key being hosted on github.